Device Lifecycle Management: A Complete Guide
Device lifecycle management (DLM) has become an indispensable practice for organizations that use a multitude of devices like computers, laptops, smartphones, tablets, printers, medical equipment, and more. With the proliferation of devices, managing them efficiently has emerged as a significant challenge. This blog post will explore what DLM entails and how it can benefit your organization.
What Is Device Lifecycle Management?
Device lifecycle management refers to the end-to-end process of managing devices throughout their lifecycle – from procurement to deployment to maintenance and eventual retirement. The goal of DLM is to maximize the usefulness of devices while optimizing costs. Essentially, it aims to ensure devices are working properly and being utilized efficiently during their service life.
DLM involves setting up policies and procedures to track devices, automate processes, maintain security, keep software updated, monitor usage, and determine optimal replacement cycles. With effective DLM, organizations can improve productivity, reduce costs, enhance security, and get the most ROI from their device investments.
Key Stages of the Device Lifecycle
The device lifecycle typically comprises five main stages:
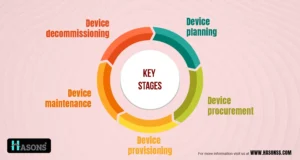
1. Device Planning
This initial phase involves assessing the organization’s device needs and constraints. Key activities include:
- Evaluating existing devices and usage
- Identifying new device requirements
- Considering compatibility issues and integration needs
- Reviewing budgets and total cost of ownership
- Assessing infrastructure readiness
- Developing policies for acceptable use, security, retirement, etc.
The planning stage allows organizations to make strategic decisions about device acquisition and management.
2. Device Procurement
Once needs are identified, the next stage is purchasing devices that align with requirements. Important steps include:
- Selecting the right devices based on needs, usability, and cost
- Standardizing models/types where possible for easier management
- Negotiating appropriate warranty and support terms
- Ensuring any custom requirements are met
- Managing relationships with vendors and suppliers
Centralizing and optimizing procurement enables organizations to acquire devices efficiently and cost-effectively.
3. Device Provisioning
After devices are procured, they need to be prepared for use. Key provisioning tasks involve:
- Tagging devices with unique identifiers
- Setting up and configuring hardware/software as per standards
- Installing required apps and security measures
- Connecting devices to networks and systems
- Testing for functionality
- Registering devices in inventory systems
- Preparing installation manuals/guidelines for users
Proper provisioning makes new devices operational and ready for use.
4. Device Maintenance
Once deployed, devices need ongoing maintenance through their active service life. This involves:
- Monitoring devices for issues – performance, bugs, damage, etc.
- Performing regular maintenance like cleaning, tune-ups, part replacement
- Managing device configurations and inventory databases
- Applying software/OS patches and upgrades
- Enforcing security policies like passwords and access controls
- Managing insurance, warranties and repair contracts
- Monitoring utilization to right-size device stocks
Proactive maintenance keeps devices running efficiently and helps maximize lifespan.
5. Device Decommissioning
When devices reach end-of-life, they need to be decommissioned properly. Key steps include:
- Flagging aged, damaged or unsupported devices for retirement
- Sanitizing devices by wiping data and restoring to factory settings
- Removing devices from networks and disconnecting services
- Updating inventory databases and deregistering devices
- Determining whether devices should be recycled, refurbished or resold
- Following environmental guidelines for device disposal
Decommissioning retires devices safely and makes way for newer tools.
Key Phases of Device Lifecycle Management
Within the broader lifecycle stages, DLM involves several ongoing phases:
Inventory Management
Maintaining a central, up-to-date inventory of all devices is crucial for tracking and managing them efficiently. Inventory management entails:
- Recording details like make/model, serial numbers, specifications
- Tracking locations and users for each device
- Tagging devices with barcodes, RFID tags or other identifiers
- Recording status – active, inactive, damaged, lost/stolen
- Updating records throughout the device lifecycle
Automation
Automating repetitive DLM tasks is key to reducing the administrative workload. Potential areas to automate include:
- Device procurement – ordering, provisioning, shipping
- Device setup – configuring standard settings
- Software installation and patching
- Warranty and license renewals
- Backup and recovery
- Decommissioning and recycling
Monitoring and Analytics
Collecting usage data provides valuable insights that can optimize DLM. Key aspects to monitor include:
- Performance – crashes, response times, capacity issues
- Utilization patterns – apps used, features accessed
- User behaviors – productivity patterns, waste indicators
- Security events – unauthorized access attempts, malware
- Support metrics – frequency and nature of help desk tickets
Policy Enforcement
DLM policies related to access controls, approved use, data security, retirement criteria etc. need consistent enforcement. Methods include:
- Implementing access rules through identity management tools
- Deploying device management agents to enforce configurations
- Blocking unauthorized apps/web services
- Automating policy application via scripts
- Regular user education and attestation to policies
Following best practices at each phase results in a streamlined, end-to-end DLM program.
Benefits of Effective Device Lifecycle Management
Implementing DLM provides significant advantages, including:
Increased Cost Savings
Proactively managing devices helps optimize procurement costs, increase useful lifespan, and lower maintenance/support overheads – leading to considerable cost savings.
Enhanced Security
DLM ensures devices are secured through access controls, data encryption, malware protection, OS patching, timely retirement etc. This strengthens the security posture.
Improved Compliance
Documenting devices and their users, enforcing asset management policies, and proper end-of-life disposal enhances compliance with regulations.
Higher Productivity
With automated deployment and fewer performance issues, workers spend less time waiting for resources. Well-managed devices also experience less downtime.
Better User Experience
Up-to-date software, properly configured tools, timely replacements etc. enable users to leverage devices more effectively for their work.
Lower Environmental Impact
Reusing, refurbishing, recycling retired devices and disposing e-waste responsibly reduces environmental footprint.
For most organizations, the gains of implementing DLM significantly outweigh the effort involved.
Mobile Device Lifecycle Management
Mobile devices like laptops, tablets and smartphones have unique management needs due to their portable nature, frequent user turnover and constantly evolving technologies.
Key aspects of effective mobile device lifecycle management (MDLM) include:
- Selecting durable, enterprise-grade mobile devices with required features
- Enforcing strong passwords/locks to protect data on lost or stolen devices
- Using mobile device management (MDM) tools to configure settings remotely
- Automating mobile OS updates to improve security and performance
- Using containers or virtualization to separate work and personal data
- Remotely wiping devices when users leave the organization
- Evaluating utilization patterns to develop mobile equipment refresh cycles
- Leveraging buy-back or trade-in offers from vendors to offset upgrade costs
With smartphones now preferred for work by many employees, capable MDLM is a must-have.
IoT Device Lifecycle Management
The proliferating use of connected Internet of Things (IoT) devices also necessitates sound lifecycle management. This becomes especially critical given IoT devices collect and transmit data that is often sensitive.
Effective IoT device lifecycle management involves:
- Assessing devices for security – encrypted data transfer, vulnerability scanning etc.
- Isolating IoT systems from other networks if feasible
- Tracking locations and ownership of distributed IoT devices
- Disabling unused interfaces to minimize attack surface
- Applying timely firmware/software updates to fix vulnerabilities
- Detecting and responding to security incidents rapidly
- Decommissioning IoT safely – factory reset, removing from networks
- Destroying devices completely when required to prevent data leaks
With the number of connected devices multiplying, securing the IoT lifecycle is a key imperative.
Why Is Device Lifecycle Management Important?
Some key reasons why actively managing devices over their lifecycle has become critical:
- Proliferation of devices strains IT resources if not managed efficiently
- Lost or stolen devices put data at risk without proper controls
- Outdated, vulnerable software presents security threats
- Poorly utilized devices represent wasted investments
- Lack of support for older devices causes worker downtime
- Non-compliance with disposal regulations can incur fines
- Ad hoc management leads to user frustration and loss of productivity
For optimal utilization, security and compliance, proactively implementing DLM is no longer optional.
Getting Started with Device Lifecycle Management
Transitioning to a comprehensive DLM approach may seem daunting initially. Here are some tips to begin effectively:
Gather Asset Information – Start by auditing existing devices to compile details into a central inventory system. This provides a baseline to work from.
Standardize Purchasing – Determine standard models to procure for each user group to streamline acquisition and support.
Automate Deployment – Tools like Microsoft Endpoint Configuration Manager can automate device imaging, configuration, patching etc.
Track Usage – Monitoring asset utilization reveals opportunities to optimize the device portfolio.
Review Security – Identify and address security gaps to protect devices and data.
Formalize Policies – Document DLM processes and policies to ensure consistency.
Seek Employee Feedback – Get input from users to identify pain points and improve their experience.
Consider DLM Tools – Solutions like VMware Workspace ONE help organizations manage devices holistically across the lifecycle.
Starting with a pilot DLM project helps build expertise. The benefits will spur further adoption across the organization.
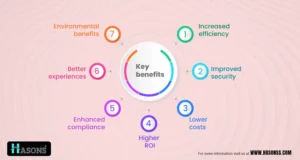
Key Benefits of Implementing Device Lifecycle Management
Some top reasons why properly implementing DLM makes good business sense:
Increased Efficiency
Automating repetitive tasks like device setup, maintenance, replacement etc. lets IT teams focus on strategic initiatives rather than routine administration.
Improved Security
Actively managing devices and applying security policies minimizes vulnerabilities. Quickly decommissioning outdated equipment also reduces exposure.
Lower Costs
Optimizing the number of devices, extending usefulness, and disposing or reselling retired equipment reduces capital and operating costs.
Higher ROI
Monitoring utilization identifies underused or redundant devices so they can be reallocated or retired – improving overall ROI.
Enhanced Compliance
Processes like standardized data wiping and responsible recycling help demonstrate compliance with regulations.
Better Experiences
Well-managed devices help users be more productive. Automating deployment and upgrades also improves user satisfaction.
Environmental Benefits
Proper disposal, refurbishing, recycling and reuse of old equipment reduces environmental impact.
With tangible benefits across the board, DLM should be a best practice rather than an afterthought.
Creating Your Device Lifecycle Management Policy
A well-defined DLM policy provides clear direction for the program. Elements to include:
- Scope – types of devices covered
- Roles and responsibilities – procurement, support, retirement etc.
- Processes for key stages – provisioning, maintenance, disposal
- Performance criteria – uptime, utilization levels etc.
- Standard models and configurations
- Compliance requirements – data security, asset tracking
- Access controls and acceptable use rules
- Retirement criteria based on age, performance etc.
- Data retention and destruction requirements
- Budget allotments for replacement cycles
- Reporting requirements to track metrics
Having documented policies ensures consistency and accountability. Reviewing them annually identifies areas for improvement.
How Are MDLM and Mobile Device Management Different?
Mobile device lifecycle management (MDLM) focuses specifically on cellphones, tablets and laptops. It covers their entire lifecycle from purchase to retirement.
In contrast, mobile device management (MDM) is software that remotely secures, monitors and manages mobile devices. MDM capabilities like wiping data on lost devices or enforcing passcodes are useful parts of MDLM.
So MDLM is the overall process while MDM is a tool used within it. MDLM determines how many mobile devices are needed and when to replace them. MDM enables administering those devices efficiently through automated controls. Together they enable comprehensive mobile asset management.
Types of Device Lifecycle Management Solutions
Several categories of solutions are available for managing different aspects of the device lifecycle:
Inventory Systems – Tools like Lansweeper that track hardware and software assets across an organization.
MDM Software – Products like VMware AirWatch that secure and manage mobile devices.
IT Asset Management – Solutions like ServiceNow that help oversee IT assets and contracts.
DLM Suites – Integrated platforms like Ivanti that cover the end-to-end lifecycle.
PC Lifecycle Tools – Solutions like Dell KACE that are optimized for managing PCs and laptops.
IoT Management – Tools like AWS IoT Core that administer connected IoT devices.
With the right solutions in place, organizations can transform device management from a costly headache to a source of productivity and value.
For more Details read Blog post Entre Technologies.
Conclusion
To gain the greatest benefits from technology investments, organizations must go beyond the initial device deployment and take a big picture, proactive approach to managing the complete lifecycle. DLM provides a strategic framework to track assets, automate maintenance, optimize utilization, keep data secure and ultimately maximize ROI across the device portfolio. While implementing comprehensive DLM takes considerable effort, the long-term dividends make it a crucial business practice.
| If you are Reading Device Lifecycle Management then also check our other blogs: | |
| CMOS Battery | Component of computer Network |
| Ports and connectors | Types of workstation |
Device Lifecycle Management
- What is the difference between device lifecycle management and mobile device lifecycle management?DLM covers managing the complete lifecycle of all types of IT equipment - including desktops, servers, printers, IoT devices etc. MDLM focuses specifically on mobile equipment like smartphones, tablets and laptops.
- What are some key challenges with implementing DLM?Key difficulties include managing numerous different device models, budget constraints for upgrades, lack of automated tools, ensuring legal/regulatory compliance and keeping pace with changing technologies.
- Why is IoT device lifecycle management important?IoT devices transmit large volumes of data, often sensitive. This makes it critical to assess and secure them properly, monitor for issues, apply timely updates and decommission them safely. This reduces the risks of data leaks and vulnerabilities.
- How can organizations improve their DLM programs?Ways to enhance DLM include increased automation, centralized inventory tracking, implementing stronger access controls, scheduling preventative maintenance and streamlining procurement with standardized models.

Thanks for sharing. I read many of your blog posts, cool, your blog is very good.