Characteristics of Firewall
Firewalls are a crucial component of any organization’s cybersecurity strategy. As the primary defense against external threats, firewalls employ a variety of techniques to control and monitor incoming and outgoing network traffic. In this comprehensive guide, we’ll explore the core characteristics of firewall and the capabilities of modern firewalls.
What is a Firewall?
A firewall is a network security device or software application that monitors and controls network traffic based on a defined set of security rules. Firewalls act as a barrier between your internal network and external networks, such as the Internet. They allow or block traffic based on factors like the protocol, port, source IP address, destination IP address, and more.
The primary functions of a firewall include:
- Filtering traffic to allow or block access based on source, destination, protocol, port, etc. This prevents unauthorized access and stops malicious traffic.
- Obscuring information about your network and systems from the outside world. Firewalls hide your internal IP addresses and other details.
- Providing a single point of control for security between networks. All traffic must pass through the firewall, allowing consolidated control and security policy enforcement.
- Logging traffic details for analysis and detecting network-based attacks. Firewalls provide visibility into who is accessing your network and what they are trying to do.
By carefully configuring the firewall rule set, network administrators can selectively allow or block traffic and create a tightly controlled access policy for their networks. This provides robust protection from many types of external cyber threats.
How Does a Firewall Work?
Firewalls use one or more filtering methods to control traffic. The most common techniques include:
Packet filtering:- With packet filtering firewalls, traffic is examined at the network protocol layer and allowed or blocked based on source/destination IP addresses, protocols, and ports numbers. This doesn’t inspect the actual packet contents beyond the header.
Stateful inspection:- Stateful firewalls not only examine individual packets but also monitor connections by remembering the status of network connections. This allows them to differentiate legitimate packets for existing connections from suspicious traffic.
Application-level gateway (Proxy server):- This type of firewall verifies contents at the application layer, not just the network layer. The firewall effectively bridges connections between internal and external networks by receiving and analyzing the actual data. This provides deep inspection capabilities.
Next generation firewall (NGFW):- NGFWs combine traditional firewall capabilities like packet filtering with deeper traffic analysis techniques, including intrusion detection and prevention. They can detect and block sophisticated application-layer attacks that simple packet filters would miss.
Firewalls use a clearly defined rule set to examine traffic and make allow/deny decisions about access. Anything not explicitly allowed by a firewall rule is blocked. By default, firewalls take a “deny all” stance and administrators must explicitly allow specific types of traffic that are required.
The firewall rule set is based on factors like:
- Source and destination IP addresses
- Network protocols (TCP, UDP, ICMP, etc.)
- Port numbers
- Applications
- User identity
- Geographic location
- Time of day
- And many others
Carefully crafted rules allow administrators to enforce granular access policies tailored to their specific security needs.
Types of Firewalls
There are several classifications of firewalls based on where they are deployed and how they filter traffic:

Network-Based Firewalls
Packet filtering firewall – A packet filtering firewall examines traffic at the network layer (layer 3 of the OSI model) and allows or blocks packets based on source/destination IP addresses, protocols, and port numbers. As noted above, this doesn’t inspect the actual packet contents beyond the header. Packet filtering provides high performance but low-level of security.
Stateful inspection firewall – Stateful firewalls monitor connections and remember session states to differentiate legitimate traffic from suspicious packets. This provides additional protection over simple packet filters by analyzing connections rather than just individual packets. Popular stateful firewall options include Cisco ASA and Palo Alto Networks.
Next generation firewall (NGFW) – As discussed earlier, NGFWs combine traditional firewall capabilities with deeper traffic analysis techniques for detecting sophisticated threats at the application layer. In addition to inspecting packet headers, NGFWs examine packet contents to block attacks like malware downloads, exploit payloads, and infected file attachments. Leading NGFW vendors include Check Point, Fortinet, and Barracuda.
Web application firewall (WAF) – A WAF is designed specifically to protect web applications and APIs by analyzing HTTP/S traffic. WAFs detect and block common attacks against web apps like cross-site scripting (XSS), SQL injection, command injection, and more. WAFs can be implemented as dedicated hardware, virtual appliances, cloud services, or modules in application delivery controllers.
Host-Based Firewalls
The firewall solutions above focus on network perimeter security. Host-based firewalls secure individual hosts or endpoints:
- Windows Firewall – The built-in firewall included with Microsoft Windows provides stateful packet filtering to monitor traffic in and out of the host computer.
- Linux iptables – Netfilter/iptables provides host-based firewall capabilities for Linux operating systems. Tables of security rules can filter traffic and masquerade internal IP addresses.
- Third-party firewalls – Endpoint security suites from vendors like Symantec, McAfee, and Trend Micro include host firewall components to control traffic at the endpoint level.
Cloud Firewalls
Major cloud platforms offer managed firewall services including:
- Amazon Web Services (AWS) security groups – Virtual firewalls can control traffic in and out of AWS resources like EC2 instances and VPCs.
- Microsoft Azure firewall – Azure firewall policies secure virtual networks with stateful packet filtering, intrusion detection, and identity-based controls.
- Google Cloud firewall – Cloud firewall rules manage connections between resources like VMs, serverless applications, and services.
These integrate natively with other cloud security controls.
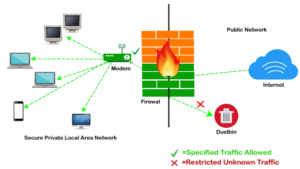
Key Characteristics of Firewalls
There are several core features common to most firewall implementations:
1. Traffic Filtering
The primary function of any firewall is filtering incoming and outgoing network traffic based on a defined policy. As traffic passes through the firewall, each packet is examined and matched to the criteria in the ruleset to determine whether it should be allowed or blocked.
Sophisticated firewalls can filter on various packet attributes like IP address, protocol, port number, ports and connectors and even application or website category. Traffic filtering enables administrators to control what types of connections are permitted for enhanced security.
2. Access Control
Firewalls govern access between network zones by allowing specific types of traffic to pass while explicitly denying all other traffic. For example, a firewall can be configured to allow only web traffic on port 80/443 between a private network and the internet.
By default, everything else incoming or outgoing would be denied – controlling external access to the network. Firewalls grant access based on protocol, IP address range, subnet, and other criteria.
3. Network Segmentation
Internal firewalls can subdivide large private networks into smaller segments. This provides perimeter security for the intranet, restricting lateral movement between departments, branches, etc. Network segmentation contains threats and limits the impact of breaches.
4. Security Logging & Monitoring
Modern firewalls provide robust logging capabilities, recording network events like blocked connections or policy violations. Logging and reporting enable administrators to monitor activity, analyze trends, and be alerted about suspicious traffic.
5. Stateful Inspection
Stateful inspection firewalls maintain context about active connections, allowing return traffic for established sessions while dropping other packets that don’t match any approved flows. This dynamic filtering provides better protection compared to static packet filtering.
6. SSL/SSH Inspection
Many firewalls can decrypt outbound encrypted traffic, scan its contents, and then re-encrypt before forwarding permitted connections. Decryption defeats threats trying to conceal malicious payloads within encrypted tunnels.
7. IPS/IDS Integration
Some next-gen firewalls integrate intrusion prevention systems (IPS) and intrusion detection systems (IDS) for deeper traffic analysis to detect behavioral anomalies and known threat signatures. This provides advanced threat defense.
User Identity Integration
Integrating with directories or SSO providers allows firewall rules to be written based on user identity rather than just IP address. This enables policies that follow users regardless of device or network location.
The Critical Role of Firewalls
Firewalls deliver a crucial set of capabilities for securing private networks:
- Defending against external attacks by allowing only safe, approved traffic flows.
- Containing threats and stopping lateral movement between network segments.
- Providing visibility through robust logging and reporting.
- Shielding devices with weak security postures.
- Enabling policy enforcement based on users, groups, applications, and content.
For these reasons, firewalls have become mandatory for the perimeter security of virtually all modern networks. As cyber threats grow more prevalent, firewalls will continue serving as the primary barrier against malicious actors seeking access to sensitive systems and data.
Conclusion
Firewalls have evolved from simple packet filters into advanced, multifunctional systems. Key firewall capabilities like stateful traffic filtering, user-based access control, and SSL inspection provide indispensable protection for today’s networks.
Understanding the core features and technologies of modern firewalls assists organizations in designing robust security architectures aligned to their specific risk profile and compliance obligations. Firewalls must be actively configured, monitored and tuned by security teams to maximize their effectiveness as part of a defense-in-depth strategy.
| If you are reading Characteristics of firewall then also check our other blogs: | |
| Desktop without CPU | Father of Personal computer |
| Storage device | SSD for Desktop |
| Hard disk Drive | Types of Cooling |
Characteristics of firewall
- What are the main types of firewalls?The most common firewall types are packet filtering, stateful inspection, next-generation, proxy, cloud, and wireless. Each uses different filtering methods optimized for various security objectives
- What are the three key functions of a firewall?The core firewall functions are defining and enforcing access control policies, segmenting the network into secure zones, and providing robust logging/monitoring of network activity.
- Which is better hardware or software firewall?Hardware firewalls offer better performance for high-volume traffic, while software firewalls provide more configuration flexibility. Many organizations use a combination of both for defense-in-depth.
- Are firewalls effective against all cyber-attacks?Firewalls are extremely effective at filtering perimeter traffic against known threats. However, they must be complemented with other tools like IPS that defend against zero-day exploits.
- Firewalls are extremely effective at filtering perimeter traffic against known threats. However, they must be complemented with other tools like IPS that defend against zero-day exploits.Firewalls are extremely effective at filtering perimeter traffic against known threats. However, they must be complemented with other tools like IPS that defend against zero-day exploits.
