Cloud Computing Security Architecture
Cloud Computing Security Architecture entails the security of data and safety in cloud services. It focuses on deploying, operating, and controlling protection procedures for information in the cloud environment.
Understanding the security of the cloud
Security is a paramount issue when engaging in any cloud computing activities. If you are relying on cloud services, your data must be safeguarded and safe. This can be done through proxy and brokerage services where clients can be prevented from gaining direct access to shared data. However, data must be stored in an encrypted format so that anyone other than the intended recipient cannot access it.
There must be a security planning phase or procedure to undertake before migrating any asset to the cloud environment. This includes assessing the risk tolerance level of the resource and identifying the right cloud service model, including IaaS, PaaS, and SaaS. In each of these models, the customer is expected to take some form of responsibility for security at that level.
Another factor that can be considered important is getting to know the kind of cloud deployment. Some types of cloud are public, private, community, and hybrid cloud. This means that the two types also have different levels of security concerns. Regarding data storage and transfer, it is also essential to consider how a cloud service provider works. The level of risk in cloud deployment is predicated by the specific service model and cloud type to be used.
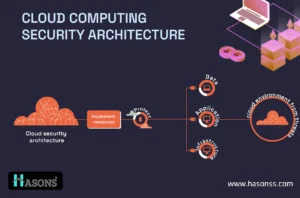
Elements of Cloud Computing Security Architecture
In terms of defining security boundaries in cloud services, the CSA stack model plays a major role. This indicates the division of responsibilities between the service provider and the user of the service.
- IaaS comes first, followed by PaaS and SaaS to provide different levels of services to the users.
- Every individual service is treated as inheriting the security issues of the layer below it.
- IaaS delivers the foundation, PaaS provides the platform, and SaaS serves the runtime environment.
- IaaS has the least integrated functionality & security, whereas SaaS has the maximum incorporated functionality and security.
- Practical security measures that exist outside the security perimeter should be managed by the customer.
Cloud Security Architecture and Shared Responsibility Model
Cloud security architecture is not something that is done by one individual on his or her own. In most organizations, a major percentage of information technology assets will still exist in their data centers, local area networks, and virtual private networks. Such responsibilities come in addition to other responsibilities that are decentralized between the customer and the cloud provider when using cloud services. This is referred to as the shared responsibility model.
In this model, the responsibilities of security tasks are shared between the cloud service provider and the users. Every component in a Cloud Server application is given to either the provider or the client, depending on the control of that particular component. This division assists in the demarcation of responsibility and guarantees that all areas of security are well addressed.
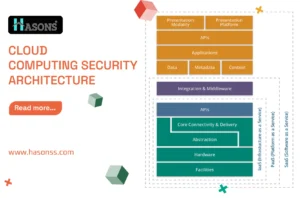
Cloud Computing Security Architecture: Types, Elements, Framework, and Benefits
Cloud security architecture involves several key elements:
Access Control: This guarantees that only the right people can access the information being collected.
Network Security: Safeguards the cloud networking service that connects the cloud services.
Application Security: They ensure the applications execute on the cloud without any security issues.
Contractual Security: Contracts all those legal requirements and details that each party’s security obligations pertain to.
Monitoring: Monitoring and surveillance to identify security threats and ensure timely intervention.
When put together, cloud security architecture offers a holistic and sound security solution. Some of the major benefits are being mentioned below:
- Easier to manage security
- Better data handling
- Stronger security protections
- Easier to update and change
- Improved disaster recovery
- More reliable and scalable
- Lower IT costs
Understanding Data Security
One of the primary challenges in cloud computing is data security, as all data is transmitted online. Hence, there are several aspects involved in the cloud that mainly protect the data from being leaked or used for corrupt purposes.
Access Control: Sets restrictions on the use of the data.
Audit Trails: It is recorded by identifying who has used the data, also what has been done with it.
Certification Authority: Ensures that only the right individuals or organizations have access to the data.
These security mechanisms assist in preventing unauthorized individuals from accessing data and also assist in maintaining the data’s integrity.
Separate Access to Data
It is crucial to keep the data separated, also avoid direct access by clients to prevent data compromise. Otherwise, the data will remain very vulnerable with several possible chances of exploitation. Hence, access control is one of the most practical ways to keep the data safe in most situations.
Broker: Can access the storage without directly interacting with the clients.
Proxy: Requires the client and the broker connection without storage access.
Conclusion
Consequently, the main security architecture of cloud computing is crucial for securing data and applications in the cloud. It comprises several safeguards that prevent various risk types and protect data from unauthorized access, modification, also loss. It is noteworthy that the protection is not only the cloud providers’ responsibility but the customer’s as well. Implementing strong standards for security and following the guidelines can significantly improve the defense against breaches, meet the legal requirements, and increase the user’s confidence. You need to take cloud security as one of the most important factors. In case you are not able to understand the details of cloud security, contact any professional who has the knowledge and experience of Cloud platforms.
| If you are reading Cloud Computing Security Architecture then also check our other blogs | |
| How to Upgrade Computer Memory | Technology Innovation |
| COPA Full Form | Pros of technology |
Cloud Computing Security Architecture
- 1. What is cloud computer architecture?Cloud computer architecture refers to the structure of computing resources, servers, storage, and even software based on cloud technology.
- 2. What are the main components of cloud computer architecture?It includes the client terminal (user interface), servers and storage, cloud services, and the network between all these elements.
- 3. What are the different cloud deployment models?They are the public cloud, which delivers services over the internet, private cloud which is used by only one organization, the hybrid cloud which is a combination of public and private clouds and the community cloud which is used by several organizations.
- 4. What security considerations are important for cloud computer architecture?Areas of security concern are data confidentiality, access issues, legal requirements, and threat prevention with the help of security devices.
