Proxy Server
A proxy server acts as an intermediary between client devices and the internet. It sits between a device, such as a computer, smartphone, or other networked device, and the wider internet. Proxy servers provide a number of benefits including improved security, anonymity, faster access to websites and web content, and more. In this complete guide, we’ll discover the whole lot you want to recognize approximately proxy servers from what they are and how they work to their key benefits and use cases.
What is a Proxy Server?
A proxy server is a server that acts as an intermediary for requests from clients seeking resources from other servers. Clients hook up with the proxy server, inquiring for a few service, which includes a file, internet page, or different resource, to be had from a unique server. The proxy server evaluates the request in line with its filtering rules. For example, it could clear out out site visitors via way of means of IP cope with or protocol. If the request is verified through the filter, the proxy gives the aid through connecting to the applicable server and soliciting for the provider on behalf of the client.
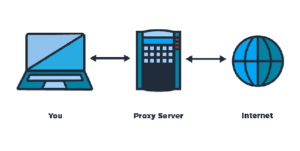
To the client, it appears that the proxy server is the actual server providing the requested resource. In reality, the proxy server is only fetching the resource on behalf of the client and returning it. This allows the proxy server to filter requests, log or audit activity, cache resources, and more.
How Does a Proxy Server Work?
Proxy servers work through a simple mechanism. When a client device makes a request to access a resource on a separate server, such as visiting a website, the request is routed through the proxy server instead of the client connecting directly to the destination server.
The proxy will evaluate the request according to its rules and filters to determine if it should forward it on to the destination server. If allowed, the proxy server makes the request to the destination server on behalf of the client. When the destination server returns the requested resource, such as loading the website, this information is routed back through the proxy to the client.
From the client side, the process is largely invisible. The client device only interacts with the proxy server and does not need to know about the actual destination server. This allows the proxy to act as a gatekeeper for resource requests and hide the identities of devices making requests.
Benefits of Using a Proxy Server
There are many benefits to using a proxy server, including:

1. Anonymity and Privacy
Proxy servers hide the IP address of the client device making requests. This helps improve privacy and anonymity while using the internet. Instead of the destination server seeing the IP of your device, it only sees the IP of the proxy server. This prevents the sites you visit from tracing behavior back to your specific device.
2. Improved Security
Proxy servers provide a firewall between your internal network and external networks. This allows proxy administrators to implement security measures, filters, and auditing to protect devices within the network. Proxies can block known malicious sites, filter suspicious traffic, and stop distributed denial of service (DDoS) attacks.
3. Caching and Improved Speed
Proxy servers can cache frequently accessed resources. When clients request these cached resources, shared proxy server can deliver them directly, improving speed and performance. The cache also reduces bandwidth requirements.
4. Content Filtering
Proxies allow administrators to control web traffic. They can block access to specific sites and filter requests based on protocols, URLs, or keywords. This provides oversight and governance of how internal networks access web resources.
5. Load Balancing
For busy servers, proxy servers can act as an intermediary to distribute client requests across multiple servers. This improves performance by sharing the workload.
6. Logging and Auditing
Proxies provide a point of control for traffic that allows administrators to log and audit access requests. This provides data on usage patterns and activity that can be used to optimize networks or identify suspicious behavior.
Types of Proxy Servers
There are several different types of proxy servers that each work in slightly different ways:
Forward Proxies
A forward proxy sits between internal client devices and external servers, such as web servers. Forward proxies are commonly used by organizations to control and monitor outbound traffic from internal networks to the internet. All client devices are configured to route requests through the forward proxy which can apply filters and policies as needed.
Reverse Proxies
A reverse proxy sits in front of origin servers and receives requests intended for those servers. The main purpose is to optimize content and load balancing for the origin servers. Reverse proxies can distribute requests, cache content, compress resources, and more to improve performance and speed for clients accessing the origin servers.
Transparent Proxies
Transparent proxies analyze traffic transparently and intercept connections without client devices having to be specifically configured to use the proxy. The client is unaware traffic is being routed through the proxy. Transparent proxies are commonly used for auditing and eavesdropping on connections.
Anonymous Proxy
Anonymous proxies are designed to hide the identity of the client making requests. There is no authentication or logging, allowing users to maintain anonymity. However, this also allows for misuse, making anonymous proxies controversial.
What Makes a Proxy Server Useful?
Proxy servers provide a variety of benefits that make them useful in both home and professional contexts. Some of the key reasons you should consider using a proxy include:
Improve Security
Proxy servers give you more control over network traffic and allow you to filter our dangerous or suspicious connections. Features like blacklisting known malicious sites, filtering content, and analyzing traffic for intrusions help protect devices on the network.
Stay Anonymous Online
Hiding your IP address through a proxy can allow you to maintain privacy and anonymity while accessing sites and services online. This prevents the sites you visit from tracing behaviors back to your device.
Bypass Geo-restrictions
Proxies allow you to obscure your true location, which can help circumvent geo-blocking and access region-restricted content from around the world.
Improve Network Performance
Caching resources locally and load balancing through a proxy reduces strain on your network connection and improves speed and performance, especially for frequently accessed content.
Gain Oversight Into Network Usage
Auditing and logging features provide administrators visibility over network traffic. This allows oversight into how the network is being utilized by users and devices.
Control Access
Administrators can use proxies to control and filter the sites and services that internal network devices can access. This provides governance over how your network reaches external resources.
Purpose and Functions of Proxy Servers
Proxy servers serve a variety of important networking roles and purposes:

Control and Monitoring
A core purpose of proxies is to act as a gatekeeper and intermediary for traffic moving between internal and external networks. This allows the proxy to analyze traffic, apply filters, audit logs, and block traffic if needed. Having a centralized point of control enables policies and governance.
Improved Security
By funneling traffic through a proxy server, various security measures like virus scanning, URL/content filtering, blacklisting, intrusion detection, and DDoS mitigation can be applied to protect the network. The proxy adds an extra layer of security for inbound and outbound traffic.
Caching
Caching frequently accessed content locally helps speed up access and improve performance. Users get content faster from the cache while also reducing outward bandwidth usage from repeated requests to the source server.
Anonymity and Privacy
Hiding IP addresses, encrypting traffic, and obscuring user identities are core functions of many proxy servers. Proxies provide anonymity for clients by masking their origin when making requests.
Load Balancing
Proxy servers can distribute traffic across multiple origin servers. This improves performance by sharing the workload instead of overwhelming a single server.
Circumvent Local Restrictions
Proxies allow users to evade geographical internet filters by obscuring the origin of traffic. Users can tunnel through a proxy outside their restricted region to gain access to blocked content and services.
Advantages of Using a Proxy Server
There are many compelling benefits and advantages to implementing and using a proxy server:
- Improved security – The firewall and filtering capabilities provide extra protection against web-based attacks reaching local networked devices. Important business systems and infrastructure gain an added layer of security.
- Better control and monitoring – Businesses can exert tighter control over internet usage by employees and guest devices. Monitoring traffic gives visibility into usage patterns and online behaviors.
- Increased performance – Caching and load balancing capabilities speed up access to frequently accessed content. This provides a performance boost for workers without additional infrastructure costs.
- Cost savings – The improved performance and caching reduce external bandwidth usage which drives down network connectivity costs.
- Productivity – Filters can block access to sites and content deemed inappropriate for workers. This helps ensure they remain focused and productive.
- Anonymity – Masking and obscuring IP addresses provides a layer of anonymity for devices accessing the internet. This hides geographical locations and usage patterns.
- Availability – Load balancing maintains availability of back-end servers and sites by distributing traffic across multiple points. This minimizes downtime if one system becomes overloaded.
Future Trends and Innovations in Proxy Server Technology
Proxy servers continue to evolve with new trends and innovations shaping the landscape:
- Cloud proxy – Proxy capabilities are increasingly available through cloud and software-as-a-service models. This provides greater flexibility without hardware dependencies.
- ROI tracking – Advanced analytics within proxies examine traffic to provide metrics on return on investment, such as identifying wasted bandwidth or cost savings from caching.
- Machine learning – AI and machine learning will allow proxies to better detect patterns, anomalies, and threats by learning from network traffic flows over time. This improves security and filtering accuracy.
- Encrypted proxies – The use of built-in encryption and support for SSL/TLS proxies will continue growing to secure sensitive communications through intermediary proxy servers.
- User experience focus – Performance improvements will seek to minimize proxy impacts to the user experience. End-users should feel no drag from routing through proxies.
- IPv6 compatibility – Support for IPv6 and mixed protocol environments ensures proxies work seamlessly as networks transition to IPv6 addressing.
- Residential proxies – More proxies will emerge in residential network segments to provide greater IP diversity for hiding origins.
- Speed – Increasing use of proxy caches and new algorithms will optimize proxies to deliver near real-time performance, even with heavy traffic loads.
Common Use Cases for Proxy Servers
There are many scenarios where proxy servers provide value:
Controlling Enterprise Traffic
Businesses can funnel employee internet traffic through enterprise proxies to monitor usage, limit access to unauthorized or non-work related sites, and apply security controls.
Enabling Remote Work
Proxies allow remote workers outside the office to tunnel securely into the corporate network through the proxy interface, accessing internal resources from home.
Avoiding Geolocation Restrictions
Accessing regionally limited content like television shows or audio streams often requires a proxy to spoof your location. The proxy masks where the traffic originates.
Protecting Public Wi-Fi Access
Connecting through an encrypted proxy when using public Wi-Fi hotspots prevents snooping or man-in-the-middle attacks that exploit open connections in public areas.
Maintaining Privacy
Using proxies helps preserve privacy by preventing websites and services from logging actual IP addresses and other identifying data about clients accessing them.
Shielding IoT Devices
Routing Internet of Things (IoT) and smart device traffic through proxies creates an added layer of security without directly exposing these devices to the public internet.
Security Considerations when Using Proxy Server
While proxies provide clear security advantages, there are some risks to weigh as well:
- Single point of failure – By funneling traffic through a single intermediary server, that proxy becomes a single point of failure. If it goes down, all outbound connectivity fails.
- Creating a bottleneck – Similarly, large volumes of traffic flowing via the proxy can create a network bottleneck. Slow proxies negatively impact user experience.
- Security liability – If the proxy itself is compromised by an attacker, the attacker can intercept sensitive communications and traffic by being positioned inline between clients and external networks.
- Loss of deep visibility – Routing traffic through a proxy may obscure details like client IP addresses which provide useful context and traceability. Some troubleshooting can become more difficult.
- Encryption limitations – Although growing, proxy support for encrypted protocols like HTTPS is still limited compared to direct connections. Full TLS inspection remains challenging.
- Privacy considerations – While clients gain privacy, administrators gain visibility into potentially sensitive communications flowing through the proxies under their control.
How to Setup a Proxy Server
Setting up a basic proxy server involves a few core steps:
Choose OS and Hardware
For small implementations, recycled hardware like old PCs can work. Optimize available RAM, processor cores, and NICs for larger deployments. Popular proxy server platforms include Linux, Windows Server, and BSD.
Install Proxy Server Software
Squid and HA Proxy are common options. Vendor router firmware often has proxy capabilities built-in as well. Install the proxy software and any dependencies on the target hardware.
Specify Network Interfaces
Configure the proxy server’s network interfaces so it can communicate with both internal and external networks. Traffic will flow from the internal interface to the external one.
Configure Authentication
Decide whether clients need to authenticate to the proxy. Anonymous access or IP-based authentication are common options. This controls which devices can route through the proxy.
Implement Access Rules
Define filtering rules based on IP addresses, protocols, URLs, or other criteria that control what traffic the proxy will pass through versus block.
Enable Caching
Configure the proxy server to cache types of frequently accessed content like images, videos, downloads, and web content. This improves speed and response times for users.
Test Connectivity
Verify clients on the internal network can transparently connect through the proxy to resources on external networks. Traffic should route via the proxy without issues.
Proxy Server Conclusion
Proxy servers act as intermediaries between internal networks and the open internet. They provide many key advantages including security, privacy, improved performance through caching, remote access capability, and content filtering. Proxy servers utilize different modes like forward and reverse proxy configurations to adapt to various use cases.
| If you are reading Proxy Server then also check our other blogs: | |
| Distinguish Between Intrinsic and Extrinsic Semiconductor | Device Management in operating system |
| Sensor Technology | Benefits of Digital Transformation |
